NetDiligence® Security Advisory – May 14th, 2017
WannaCry/WannaCrypt Exploit Protection Tips
This NetDiligence Security Advisory is published for the benefit of our cyber insurance carrier/broker clients and their insureds. We urge clients to take special note of the details included in this Advisory and take preventative/remedial action on a timely basis. Clients are welcomed to distribute this Advisory to their colleagues and others as they see fit, provided it is distributed without modification of its contents.
OK, so let’s get to the heart of this problem quickly – you don’t want to see this on your Windows PC screen today:
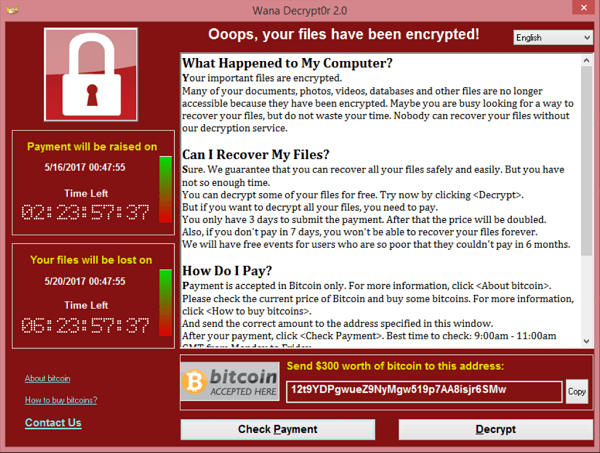
The WannaCry exploit is targeted against Windows-based systems, and is based upon malware code that was originally developed by the U.S. National Security Agency (NSA) for use in their ongoing intelligence operations.
This is one of the screen shots from the globally-launched WannaCry/WannaCrypt ransomware file encryption exploit that has infected hundreds of thousands of systems (as of the date of this Advisory) and which forces the recipient to pay a defined ransom via Bitcoin within a limited timeframe to receive a functioning decryption key – or else face the permanent loss of their files. Even if you believe that your files are safely backed up on archival storage, you must now test the actual effectiveness of that assumption and hope for a timely recovery by your IT team while the rest of your business activities come to a grinding halt.
It shouldn’t have to come to this, and our job with this Advisory is to provide timely details on the preventative steps you can take now to increase your chances of escaping this fate.
The WannaCry exploit is targeted against Windows-based systems, and is based upon malware code that was originally developed by the U.S. National Security Agency (NSA) for use in their ongoing intelligence operations. The code involved here incorporates a vulnerability in Microsoft’s decades-old Server Message Block (SMB) protocol that supports LAN-based communications, file shares, and related functions.
Knowledge of this prior code was released to the public in April, 2017, by an external hacking organization seeking to further their own advocacy goals. A derivative of the original code, now known as WannaCry, was distributed by profit-seeking individuals and reached worldwide impact/awareness on May 12th.
Microsoft had already been well aware of the risks associated with this exploit, and had published details of proactive fixes for their servers on March 14th, 2017, as described in their Security Update (MS17-010) that can be found at:
https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
Microsoft published additional articles relating to this exploit as WannaCry was making world-wide headlines in order to provide further timely details:
and…
https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
With the extra attention the WannaCry exploit has received – including reports of hospitals in the U.K. being knocked offline and forcing healthcare personnel to revert to pen and paper in their patient documentation tasks – Microsoft took the somewhat unusual additional step of providing related fixes for older versions of their operating system that were otherwise no longer being supported. These include fixes for Windows XP, Windows 8, and Windows Server 2003.
The essence of the timely advice being put forward amounts to the following:
1.If you have not already done so, ensure that Microsoft updates relating to MS17-010 are applied to your Server and end-point workstations immediately.
2. If you have one of the older, otherwise non-supported Microsoft platforms still in play, promptly review, download, test, and apply the Microsoft Update Catalog fixes that have been made available for Update KB40112598 at: http://www.catalog.update.microsoft.com/Search.aspx?q=KB4012598
3. Ensure that your current AV signature files are up-to-date and proactively deployed to all systems within your organizational environment (including remotely connected workstations). Symantec, for example, has published the following Blog entry that seeks to assist customers with their preventative efforts regarding WannaCry: https://www.symantec.com/connect/blogs/what-you-need-know-about-wannacry-ransomware
4. Ensure that your core LAN server and workstation backup and restore procedures have been thoroughly tested for full and prompt effectiveness in an on-demand situation such as a WannaCry infection might demand. As it is possible that an infection might render even a successful recovery effort less than 100% effective due to the gap between the time of infection and the time of the most recent backup event, ensure that recovery point objectives (RPOs) have been reduced to the greatest extent feasible.
5. Intrusion prevention system (IPS) solutions represent an important defense against exploits such as WannaCry via e-mail, Web access, and/or other types of entry points into your organization. Ensure that IPS systems are installed, properly configured, continuously updated, and continuously monitored for alerts and suspicious activity patterns.
6. If you are already infected with WannaCry – and while there are a number of published articles that we have seen that detail highly-technical removal steps – we are not into recommending do-it-yourself infection removal efforts. We highly recommend immediately contacting your cyber insurance carrier’s Breach Coach® (listed within your NetDiligence eRiskHub® subscription) so that they can provide a timely review of your situation and put you in contact with a qualified data forensics vendor who can properly advise upon a successful recovery stragegy from the infection. This effort may also necessitate filing a claim against your cyber insurance policy, so please ensure that your organizational Risk Manager is involved!
7. Education, Education, Education! We cannot emphasize strongly enough that educating your employees/team members as to the risks posed by phishing attacks from malicious individuals/entities represents a mission-critical element in your overall information security program. The bad guys will continue to come up with new exploits (and variations on them) that are designed to evade every technical protection (AV, IPS) that your IT team can throw at them. In the end, employees often represent the first – and last – line of defense against such exploits through knowledge and vigilance directed against these kinds of threats. In addition to formal security awareness training that is designed to promote such knowledge/vigilance, consider adding to your portfolio “social penetration testing” that incorporates intentional – but benign – phishing attacks against your employees so that they can feel for themselves the consequences of poor choices in clicking on untrustworthy e-mails. When a 30-second, blood-pressure raising warning message is followed immediately by a reassuring message that this was only an example of what *can* happen, employees value the lesson highly.
If you have been compromised by WannaCry login to your eRiskHub portal and reach out to your Breach Coach®, please use the Contact Us function if you need help getting registered or logging in.
Thank you very much for your attention to this NetDiligence Security Advisory, and please do not hesitate to reach out to us (at [email protected]) for further advice and assistance with your cyber risk management efforts!





